IPsec
Stands for "Internet Protocol Security."
IPsec is a group of protocols that help create secure connections between two devices over a network. It works on top of the standard IP protocol suite to add authentication and encryption to network traffic, whether it travels over a local network or the public Internet. It is most commonly used to establish secure connections for Virtual Private Networks (VPNs), but can help secure data transfers for many purposes.
The IPsec protocol suite consists of three protocols that work together to authenticate and encrypt IP traffic:
- The Internet Key Exchange (IKE) protocol handles negotiations between two devices (also known as hosts) to decide which algorithms to use for authentication and encryption. It also generates a secure, shared cryptographic key that both hosts can use to encrypt and decrypt data.
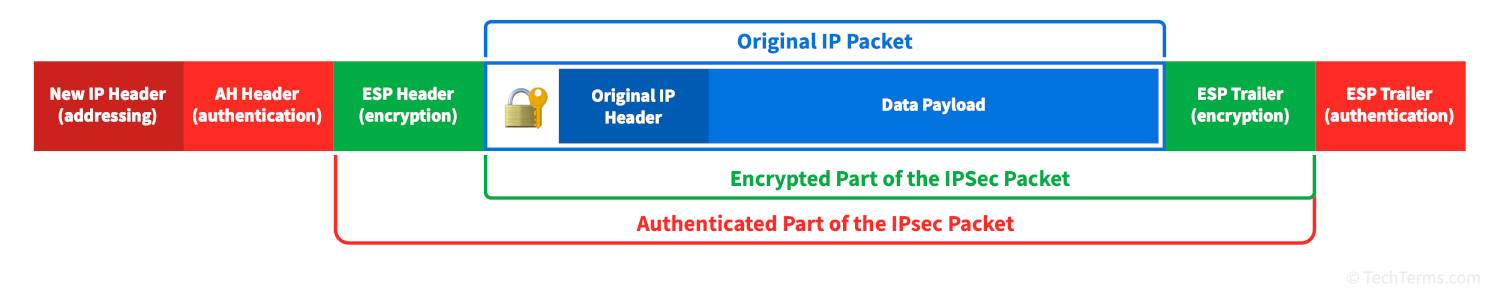
- The Authentication Header (AH) protocol adds authentication information to each data packet's header. This information includes a cryptographic hash of the packet's contents that the recipient can use to see whether anything modified the packet during transit.
- The Encapsulating Secure Payload (ESP) protocol takes a normal IP data packet, encrypts it using the agreed-upon algorithm and cryptographic key, then creates a new data packet with a new header (including the information generated by the AH protocol) that contains the encrypted original packet as its payload.
These three protocols work together to protect IP traffic end to end. The IKE protocol creates a secure connection between hosts and establishes authentication and encryption details. The ESP protocol then encrypts each data packet, and the AH protocol adds header information that routes the packet to its destination. It also ensures that the receiving device can authenticate the packet and alert the recipient if any other device intercepted it.
IPsec Modes
The IPsec protocol suite supports two modes for securely transferring data, depending on the type of network it's operating over and what kind of data it's carrying.
- Tunnel Mode encrypts the entire IP packet and encapsulates it in a new packet. This packet includes an entirely new header with the origin and destination addresses of the tunnel's endpoints —typically the routers that connect directly to the computers involved in the session. The receiving router decrypts the packet, reads its destination address, and forwards it to its destination. Tunnel mode is typically used for VPN connections and when transferring IPsec packets over the public Internet.
- Transport Mode encrypts only the contents of an IP packet, leaving the original header in place. It appends information from the AH protocol to the header for authentication but does not obscure the addresses of the origin and destination hosts. Transport mode requires slightly less overhead for each packet and is typically used when transferring IPsec packets over a local network.
 Test Your Knowledge
Test Your Knowledge