Tunneling
Tunneling is the process of transporting network traffic that uses one protocol within data packets using another protocol. It allows two devices to hide the nature of the data within the tunnel from other devices on the network. Tunneling protocols can encrypt traffic, provide a secure connection for a VPN, or allow packets using an unsupported protocol to travel across a network.
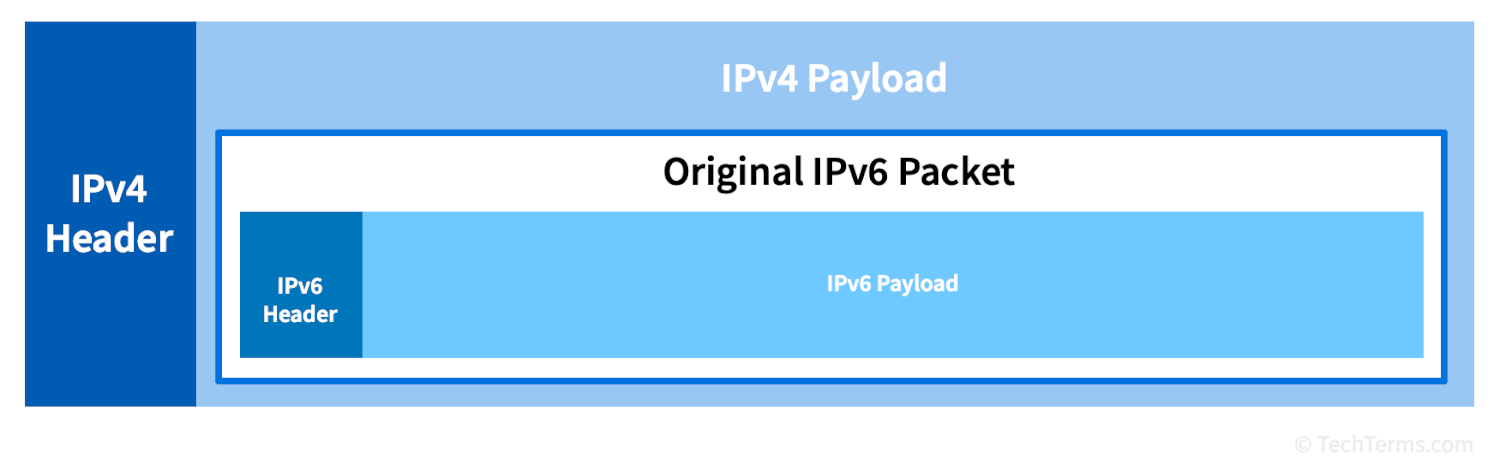
All data sent over a network travels in data packets. Each packet consists of a small header comprising protocol and address information, followed by a large data payload containing the transferred data itself. Tunneling takes an entire data packet and turns it into the payload of another data packet that uses a different protocol in a process called "encapsulation." The other devices on the network that carry a packet to its destination can only see the header of the outer packet and are unaware of the contents of the encapsulated one. Once it reaches its destination, the receiving device decapsulates the packet and accesses its data payload.
The most common use for tunneling is establishing secure VPN connections over the Internet. A VPN uses one of several tunneling protocols, like IPsec, L2TP, or PPTP, to encrypt all traffic between a VPN server and a client. However, there are other reasons that a data transfer may require tunneling. In some cases, the network may not support the original protocol. For example, if an IPv6 packet needs to travel over a network that only supports IPv4, it can be encapsulated within a compatible IPv4 packet and decapsulated once it reaches the other side.
Tunneling can also encrypt traffic using a protocol that does not support encryption by encapsulating it within a protocol that does. One example is SFTP, which creates an encrypted SSH tunnel that carries unencrypted FTP traffic. Finally, tunneling can help certain types of traffic bypass a network's firewall by encapsulating restricted traffic (like P2P file sharing) within accepted protocols (like HTTP).
 Test Your Knowledge
Test Your Knowledge