ACL
Stands for "Access Control List."
An ACL is a list of user permissions for a file, folder, or other data object. The entries in an ACL specify which users and groups can access something and what actions they may perform. ACLs are used by operating systems, networking devices, and database management software to help administer access to resources.
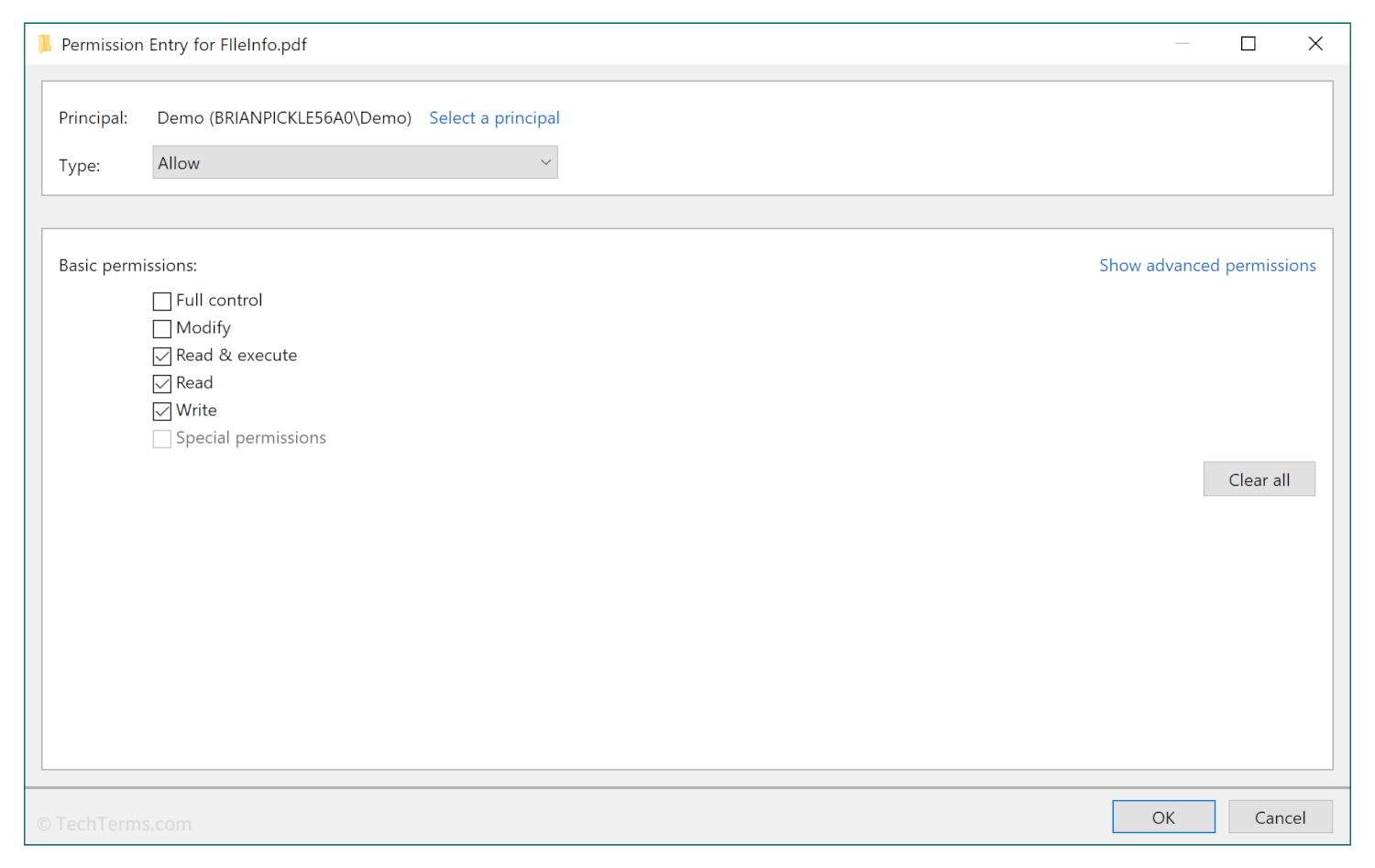
Multi-user operating systems like Windows, macOS, and Linux use ACLs to manage permissions for files and folders in the file system. These ACLs govern access for both individual users and user groups and determine what actions they may perform. On Unix-based operating systems, these operations include read, write, and execute; ACLs on Windows also support those same operations and add modify and full-control permissions.
Database management systems use ACLs to control the ability to access and modify the contents of a database. A database ACL manages access to both database objects (like a specific table or view) and to the data itself (in a table's rows and columns). Database administrators can control which users and user groups can add, update, and delete data from a database; they can even hide specific fields from certain users to keep some information secret while still allowing access to less sensitive data.
Network devices use their own ACLs to control and filter network traffic. However, instead of controlling access by users and groups, they use other criteria to decide whether to permit traffic to pass. Typical criteria include the source and destination IP address, port number, protocol, or even time of day. These criteria may even be combined to provide very fine control over network traffic. For example, a router may be configured using an ACL to block streaming video overnight while still allowing web browsing traffic to proceed.
 Test Your Knowledge
Test Your Knowledge